As phased reopening of businesses has begun in Arizona and across the country, it would be easy to relax and let your guard down at home and on your phone, with daily work and school getting back to business. But since much of our lives have transitioned to online, it’s important to remember that hackers attack when we least expect it, and now’s the time to make sure you remain cyber safe!
Email fraud is definitely a big concern, as hackers prey on us all getting comfortable. It's easier for hackers to gain access to business accounts when employees are working from home using their personal home computers and don't update their virus and malware security systems on a regular basis. In fact, business owners who have employees working from home on their own computers should assume those home computers are not safe. According to UAT President Jason Pistillo, companies can make sure they have spam filters set up appropriately, but they've got to “watch that like a hawk.”
"Many people aren't good about updating their home computers," he said. "Home computers get infected and that propagates up to the corporate network.”
In fact, email scammers even came after UAT!
It began with an email from a vendor seeking a valid payment, but when the accounting department responded to that original email, a hacker intercepted it and requested that the money be paid electronically to the hacker's account.
Our accounting department noticed something was wrong because the reply address converted to a new email with only a single different letter. "This was sneaky,” Pistillo said. “What they're doing is hijacking the requests as they go out. I don't know if anybody else would have caught it. Our accounting department is savvy. After all, they're around a bunch of hackers all day long."
Check out the full story from 12 News (the Phoenix NBC affiliate):
And from the Phoenix Business Journal:
Valley university sniffs out cyberscam before damage done.
But don’t worry, there are several ways you can be vigilant and help protect yourself.
Tom Tardy, Network Security professor at UAT, offers the following advice if you are the end-user of an email that you want to make sure is secure.

Tom Tardy Gives a Presentation About the UAT Cyber Program
1. Hover over links to see where they go, but don’t click them.
2. Make sure when you hit reply the email address is the same as the original.
3. Check your Junk Email Settings
(In Outlook, Home>Delete group>Junk>Junk email options).
a. Go to ‘adjust settings’ under each tab.
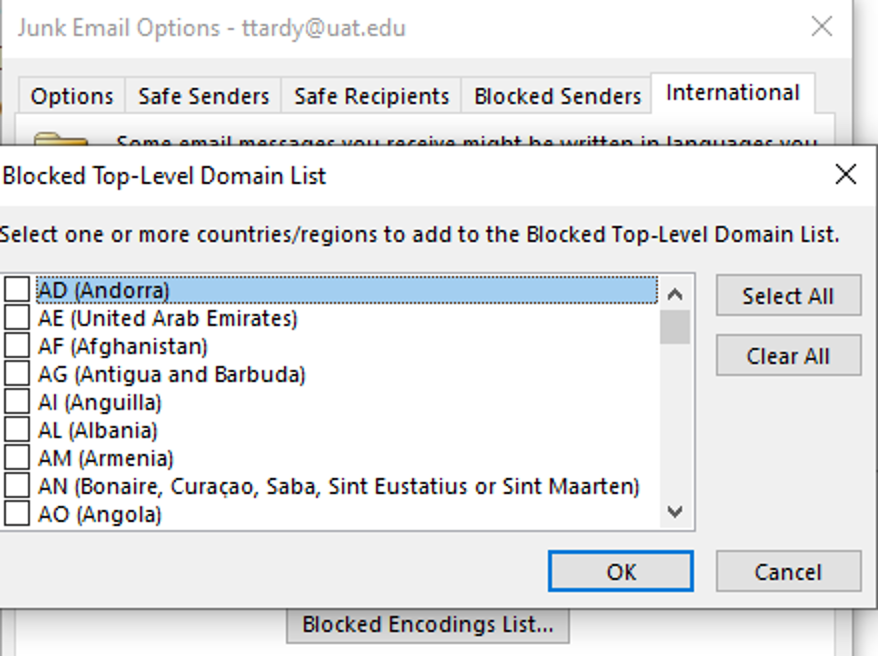
b. Block TLDs (Top Level Domains) from countries.
Emails should only be coming from a .com, .org, etc.; NOT a .cn or .ru.
c. Install Microsoft Junk E-mail Reporting Add-in (for personal email).
d. Install spam reporting Add-in (for corporate email).
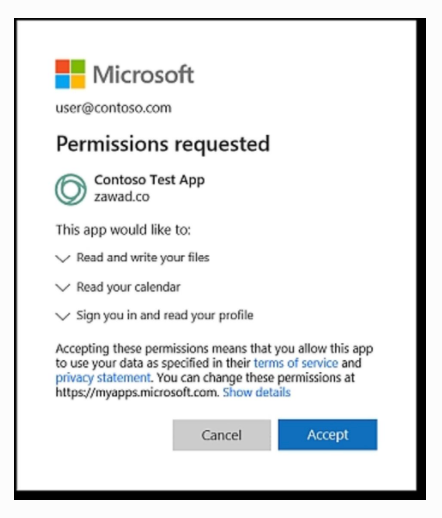
There is also a common phishing attack on organizations that use Office 365 and comes in the form of a file being shared to the user. The fake file goes to a real login page, where now—as a new trend—it then prompts the user to authorize a new application. From there it can access anything that user can access.
If you see a box like this, stop and think before you give any access. You should not need to give permission to see your contacts, emails, and other data just to open a simple file.
Jacy Smith, Business Development Specialist for Perimeter83, explains that it’s equally important to keep the account where your domain name is registered safer than usual. The Domain Name System (DNS) controls all the information where domain names send traffic to, plus controls email settings and some security information. For example, Smith says, “Many people buy a domain name for their business from a place like Go Daddy. Once they purchase the domain name, DNS is used to tell the domain where the website will be hosted (A record), where the email is hosted (MX records) and other records required to use certain services (like Office365).” Smith continues, “If a hacker were to get access to the Go Daddy account, they could alter the DNS of a domain to redirect to a malicious site, tamper with email services or decrypt encrypted web traffic.”

UAT Cyber Students Work in the Cyber Cave
She suggests the following DNS safety tips:
⇒ Take a look at the DNS records for domain names to make sure all of the records are current, accurate and appropriate for the services you or your company are using.⇒ Update passwords to the account where your DNS is managed (probably your domain host) on a regular basis.
⇒ Enable two-factor or multi-factor authentication for these accounts, if available.
⇒ If you’re unsure, contact your domain registrar (whoever you purchased their domain from) and ask tech support to review the DNS settings.
There’s always something/someone new out there, sneakier and hell-bent on hacking even through even the best attempts at safety. If you do get hacked, here are some ideas to help before taking it to an IT expert.
⇒ Disconnect from the internet.⇒ Run anti-virus scans, both online and offline (if available).
⇒ Change all of your passwords.
⇒ Enable multifactor authentication.
⇒ Don't engage with a hacker—that’s not a fight you want.
⇒ In event of ransomware, this link may help: https://www.nomoreransom.org/.
Even President Pistillo knows that hackers are smart and always lurking. “I've been doing this for 25 years, so it's not often that I'm surprised," he said. But that’s because he’s always looking, and you should be, too. Keeping your computer updated and anti-virus definitions current is just a very small piece of the cyber security picture, because the biggest vulnerability is human error. Keep your eyes open and stay cyber safe. The image of a guy in a hoodie in a dark basement is an old one… the girl next door or an average guy across the globe may be watching you right now!
Want a quick, helpful cyber security presention?
June 3, 2020, at 11am MST, join us for Technically Speaking: Don't Be Baited! Tips to Spot Phishing with Aaron Jones, Arizona Threat Liaison Officer and UAT adjuct faculty member.
Listen to learn why threat actors conduct phishing operations, how they are conducted, and how to spot phishing. Jones will discuss simple methods to protect yourself, as well as some of the tools you can employ to reduce your chances of becoming a victim.

Find out more about the Cyber Security Degrees offered at UAT!
Our cyber security degree programs and cyber security lab are recognized by industry and government entities alike for their ability to help generate the future innovators of the cyber security industry. We focus on creating true leaders who will have mastery in ethical hacking and uphold the highest industry standard of integrity in our quickly evolving world of cyber security tech and online security.
Visit https://www.uat.edu/cyber-security-degrees for more.




Comment