Removing user consent from an Azure AD application
I’ve been working with my team on refactoring the authentication process that has been put in place in the application I am working on. One of the requirements was that we wanted to test out what happens when the user sees the user consentement (that is that the user consents the application to access data on its behalf), but also, when we do not see the user consentement.
To my demise, finding out what has been granted and what has not, is not user friendly in the Azure portal. For my own sake, and perhaps yours, I will try to demystify the where and the how.
Finding out the grants
To find out what API permissions have been accepted or granted by users, for your application, in the Azure portal, is not trivial to find. To do that, you need to go in the Azure Active Directory blade, and navigate to the Enterprise applications blade. Find your application and click on it. In your application, under the security section, click on the permissions blade. Within it, you should have the user consent tab. You can then see how many users (and who) have consented to your application.
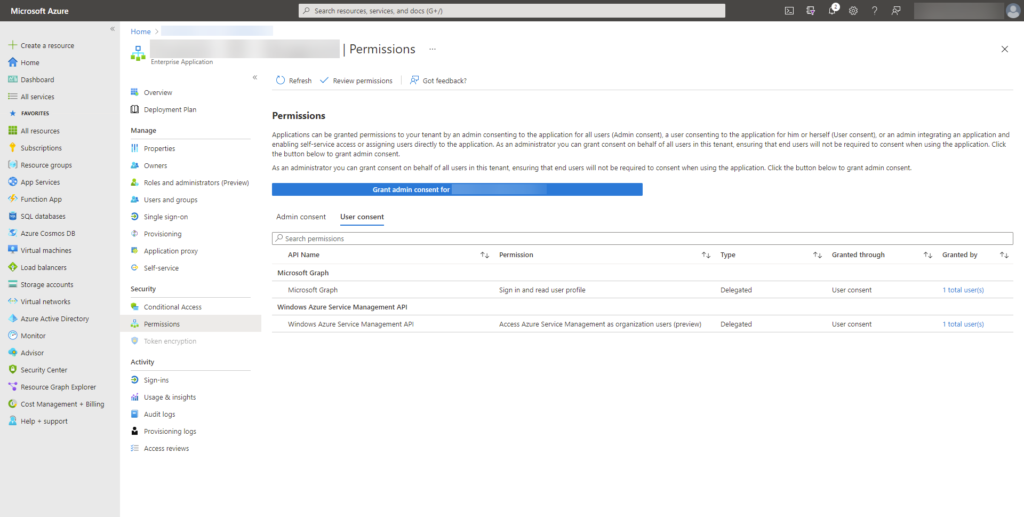
Remove the grants
Removing the grants, for a specific user, specific users or all users, cannot be done through the portal. Currently there is no UI features to remove consented permissions, PowerShell or using the Graph API is the only way. As you can see in the above picture, there are ways to play with this. If you click on Review permissions, you will see that Microsoft gives you some pointers on what can be done through PowerShell depending on your scenario.
In my case, I wanted to remove 1 user (my user) from the granted consentement.
The following example is a PowerShell script that allows the removal of 1 user who’s consented that I’ve put together. You will need the AzureAD PowerShell module. Unfortunately, due to some problematic with .NET Core, the module doesn’t work well in PowerShell 6/7.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
#Requires -Modules AzureAD [CmdletBinding()] param ( # The service principal (user) object id of the application. Can be found in the Enterprise applications->your application, under the overview blade [Parameter(Mandatory=$true)] [string] $AzureAdServicePrincipalObjectId, # The user principal object id that you want to remove the consent for [Parameter(Mandatory=$true)] [string] $UserPrincipalObjectId ) Connect-AzureAD # Get Service Principal using objectId $sp = Get-AzureADServicePrincipal -ObjectId $AzureAdServicePrincipalObjectId # Get all delegated permissions for the service principal $spOAuth2PermissionsGrants = Get-AzureADOAuth2PermissionGrant -All $true| Where-Object { $_.clientId -eq $sp.ObjectId } # Remove the consented permissions for the principal $spOAuth2PermissionsGrants | Where-Object PrincipalId -eq $UserPrincipalObjectId | Remove-AzureADOAuth2PermissionGrant |
Usage:
Note: script the name of the file that you saved the script under
Hope this helps anyone who may be in the same boat.
